HealthcareAI
The AI arms race in healthcare: Innovation without compromise
There are several key factors that healthcare organizations should consider when it comes to keeping up with the race…
Read article

Healthcare Workforce Technology
10/21/2021
by Sean Sims

The growing risk of cybersecurity incidents is well-documented. Hardly a week goes by without a major headline on the topic, and this year, it’s ransomware that has dominated the news; in particular, there were breaches at the Colonial Pipeline, meat supplier JBS, and the software company Kaseya that drew large-scale attention to the problem. It’s safe to say there are many (daily) security incidents that do not attract widespread media attention.
The healthcare industry is certainly not immune from these risks, and to make matters worse, there are some unique concerns the industry has to worry about. First and foremost is a concern about patient safety and security. Healthcare providers are increasingly reliant on highly sophisticated, connected systems to care for patients. A disruption to those systems poses a very serious risk to the standard of care that patients can receive. Healthcare providers have data privacy concerns to deal with as well: HIPAA is the obvious one, but for any organization that accepts card payments, PCI presents additional data security requirements.
A few years ago, one of our healthcare clients had a major cybersecurity incident that caught their leadership’s attention. In response, they invested millions of dollars in innovative new security technology. For healthcare organizations eager to protect their patients and data against cybersecurity threats, there are many vendors offering a wide array of different technologies. Our clients have had success implementing some of those tools, but cybersecurity isn’t only a problem to be solved by technology – it’s a problem to be solved by people. Although the human element to cybersecurity doesn’t always attract as much buzz or investment, employees make very important contributions to an organization’s cybersecurity.
Most breaches can be traced back to employee behavior. Effective cybersecurity requires regular, recurrent employee education and training. For healthcare systems large and small, every single employee presents a vulnerability, and it only takes one errant click to introduce a security compromise into the system.
Simulated phishing attacks
Employees should know how to spot a suspicious e-mail, what actions to take, and what actions not to take. Realistically, education and training is not enough to ensure adequate cybersecurity protections. Smart organizations also enforce their employee’s behavior: one common tactic is simulated phishing campaigns. Sendero has worked with multiple clients who employ this approach – they use software that allows them to circulate fake phishing attempts to their employees via e-mail. Employees are given the option to follow links, open attachments, and enter personal data (e.g., login credentials) into fake landing pages. By tracking which employees are fooled by these e-mails, the organization can require enhanced, targeted training requirements for those individuals to reduce their risk profile over time.
Password policies
Password policies require similar vigilance. Organizations should make sure their password policies adhere to industry best practices, and that they are documented and clearly communicated to all employees. As with the approach to suspicious e-mails, however, knowledge is only half the battle. It’s also important to ensure employees are following these policies. Sendero recently completed a project with one of its healthcare clients to deploy a Privileged Access Management solution to its server admins and other critical IT admins. This solution included a password vault to protect sensitive credentials and enforce adherence to password policies.
Patching programs
There are some security responsibilities that are unique to IT staff. In particular, it’s important for them to stay up-to-date with patching. When done manually, patching is vulnerable to delays and other human “errors.” However, automated patching can help the organization stick to a regular patching schedule to address security vulnerabilities. That’s especially critical for older systems. Routine patching will help remediate many threats that are “low-hanging fruit”, but some healthcare providers rely heavily on their vendors to patch and maintain equipment, including biomedical devices that are so central to patient care. For the major security incident mentioned above, our client ran into a roadblock when they realized they needed to be more aggressive with their patching protocols, but depended heavily on vendors to maintain those vulnerable devices. They resorted to a large investment in firewalls (and a segmentation strategy) to separate those vulnerable devices from the rest of the network.
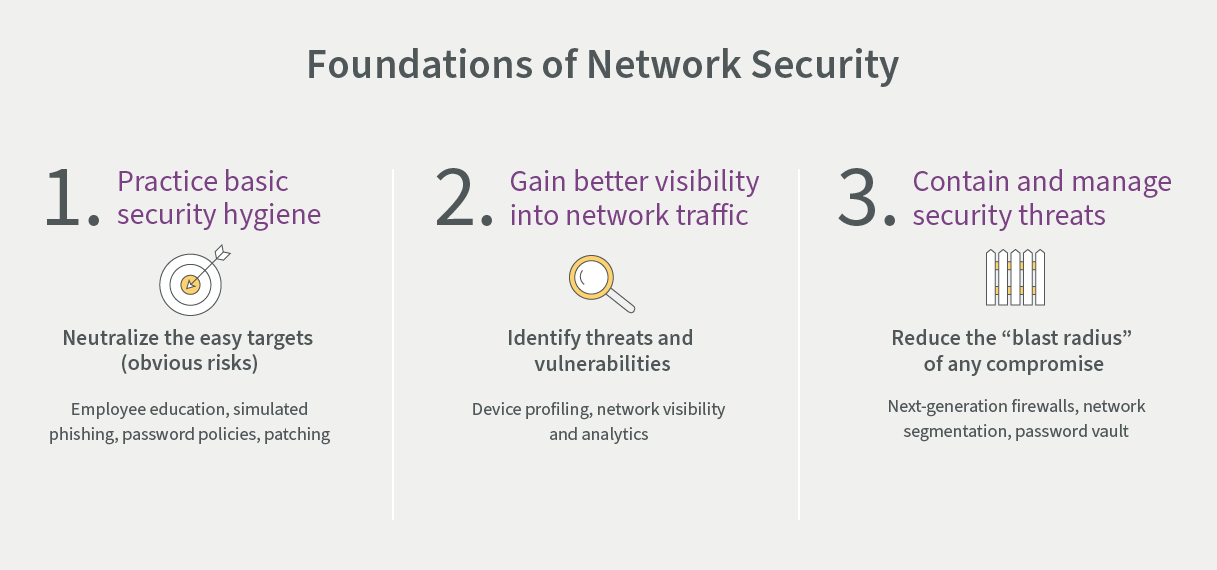
A focus on the habits and behaviors of employees will only move the needle so much. Eventually, organizations have to depend on new technology to do the rest. In particular, we’ve seen clients make recent investments in next-generation firewalls, network segmentation, device profiling, network visibility, and analytics.
With each of the tools we help our clients deploy, the implementation challenges are not exclusively technical. As one of our CISO clients is fond of saying, “all problems are fundamentally people problems,” so we find it important to employ change management tactics that balance the human side of the equation with the technological solution. It’s critical to build the organization’s capabilities to operationalize and support these new tools as the technology is successfully scaled up.
Patient safety and security should be at the heart of every healthcare system, but when there is a cybersecurity incident, that vital mission is threatened. It is tempting to throw a lot of money at these risks and purchase “shiny” new tools, but large budgets and expensive technology are only part of the answer to this global threat. The right approach must balance selective investments in innovative solutions with a “back-to-the-basics” mindset that emphasizes employees’ daily security behaviors.
If you’re facing cybersecurity challenges and would like to hear more about our client work in this area, please connect with a Sendero consultant so we can help. To stay informed on industry trends and emerging solutions, sign up for our newsletter using the “Contact Us” form at the top of this page.
Business insights
HealthcareAI
There are several key factors that healthcare organizations should consider when it comes to keeping up with the race…
Read article

Healthcare
While private equity investment in healthcare is valuable, providers should familiarize themselves with alternative…
Read article

HealthcareOptimize Technology
Advancements in health tech have allowed both patients and clinicians to experience the benefits of digital…
Read article
